Security systems and data access policies¶
Related Topics¶
Potentiality has recently further enhanced its strict security policies to take every precaution against external intrusions and to protect against hacker phishing attempts. Phishing attacks are by far the most common cause of data breaches and especially malicious data breaches on the internet ( an interesting article with some good references - https://blog.knowbe4.com/70-to-90-of-all-malicious-breaches-are-due-to-social-engineering-and-phishing-attacks ).
The usual response by companies regarding Phishing Attacks is that they educate their staff to avoid the occurrence (which we do too), but the fundamental philosophy of our new guidelines is to assume that a staff member will fall victim to some sort of phishing attempt at some stage. To assume that staff won't fall victim to a phishing attempt would be to drop your guard against these types of attacks. The following assumes that any and all breaches are possible, no matter how unlikely.
Coding practises¶
- Regular software patching
- Coders design, develop, deploy and test according to industry leading practises (such as OWASP compliance)
- Regular internal and external penetration and vulnerability testing
- Passwords are stored in an unrecoverable encrypted format
- All data is encrypted at rest and in transit
- Databases have no available direct connection with the public internet
- No credit card information is stored on Potentiality servers
- Firewalls only allow access on necessary ports
- Private data is held in localised regions to adhere with local data protection policies and stored on separate tables with unique username/password combinations per client
- Data is regularly backed up and all systems can be restored from scratch in less than an hour
- Application logs are uploaded to an external and independent data store
- Network infrastructure is zoned and access is restricted (see below)
Layers of cyber protection¶
- Amazon Web Application Firewall (blocks known untrusted sources and known general penetration attempts)
- Amazon Security Groups (limits the ports available to only those required to specific servers in DMZ)
- Local firewall (micro-server in our serverless fleet runs an internal firewall only allowing traffic in specific ports)
- Custom packet inspection (each request has the posted data analysed and matched with known formats of incoming data)
- Each micro-server runs its own Malware and Virus scanners
Potentiality employee access¶
- Potentiality employees all use virtual desktops which are locked to the employee IP address and require 2 factor authentication to access
- Potentiality employees will usually access sites through the Potentiality interface which requires 2 factor authentication and is locked to the virtual desktop IP
Direct access to live client databases is:
- only available to certain programmers
- only from within the virtual desktop environment
- only upon a request
- requests are logged per user
- access is shutdown automatically
- access is only granted to selected client data tables
Direct access to the servers and serverless resources is
- only available from within the virtual desktop environment
- only upon a request
- requests are logged per user
- access is shutdown automatically
Clients have an upload tool within their sites to transmit private data securely, ensuring data always stays within their local private data store (and not as attachments on emails)
Potentiality employees have restricted access to AWS control panels ensuring they can't alter or interfere with the network structure or backups processes
Data Access Diagram¶
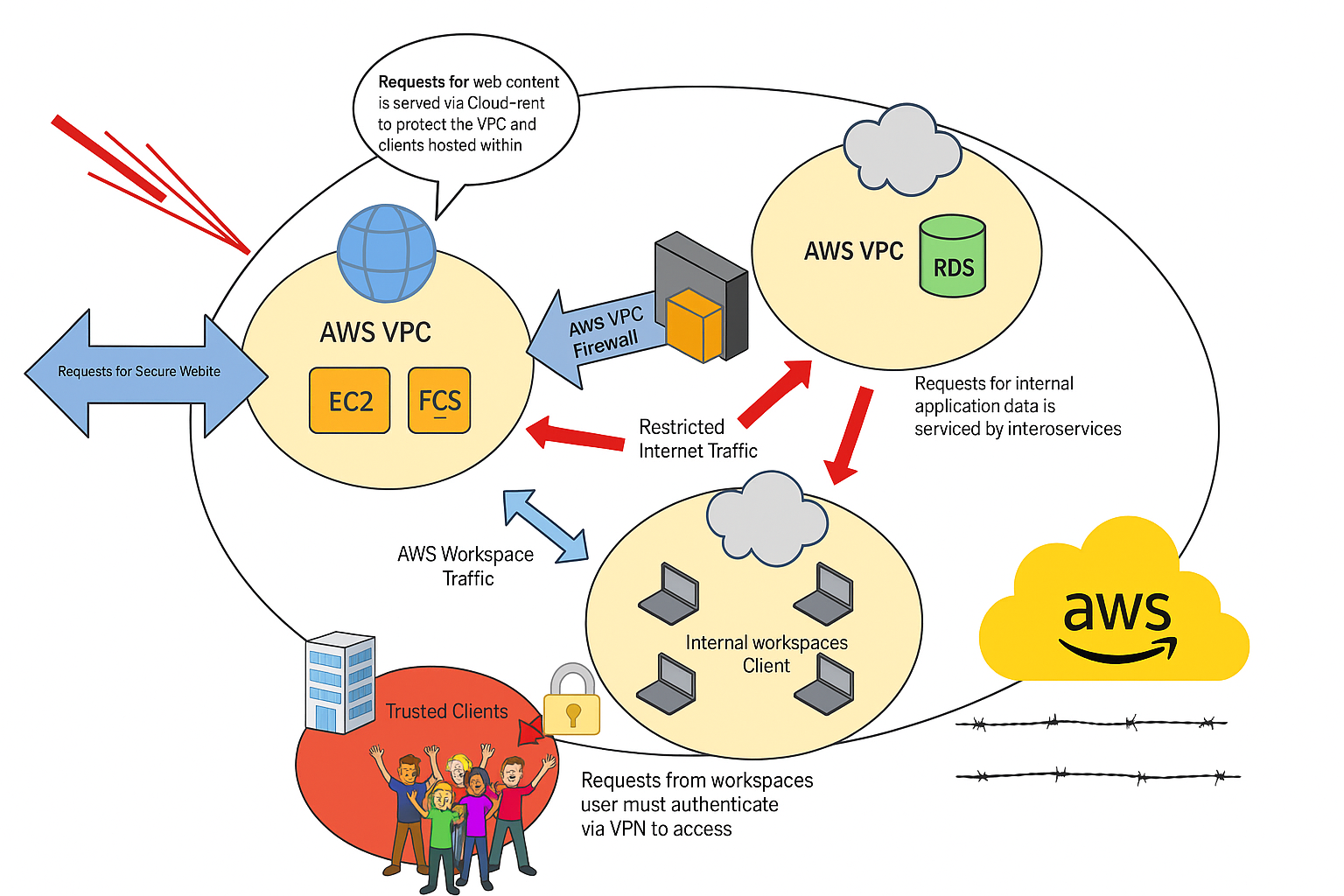
What does this protect against.¶
- Through good coding practises and robust network design we minimize (to the point of almost eliminating) the possibility of hackers gaining access through our main internet ports
- Private data is held behind 2 hardware firewalls (ignoring software firewalls) ensuring private data is protected with the highest level of security
- If computer equipment is stolen from Potentiality offices no access is available and no private data is lost
- If a Potentiality employee falls victim to a phishing scam, no access is available and no private data is lost
- Potentiality staff are unable to install unapproved software on their virtual desktops ensuring they can't be tricked into installing malware
- Virtual desktops have firewalls in operation to ensure they're protected even if another virtual desktop is compromised
- If a hacker somehow got access to a virtual desktop they would have no access to the servers or client data
- If a hacker somehow got access to a live server, the usernames and passwords for client databases aren't stored in plain text meaning they wouldn't get immediate access to any client data
- If Potentiality fell victim to a ransomware encryption attack, servers could be restored within an hour from external backups
- Application logs are held independently off site to allow for forensic analysis of any intrusion
- If a Potentiality employee with high level access went rouge and tried to access client data, other Potentiality employees would become aware of the additional access and it could be disabled
sub-pages¶
0 0